Hybrid working has become a part of workplace culture for many organizations. Dealing with a distributed workforce, multiple layers of network applications, and an increasing number of IoT and mobile devices, means that network security solutions are a top priority for every business.
Computer networks are more vulnerable than ever to cyber threats, data breaches, malicious software and intrusion by unauthorized users.
Of course most businesses have some sort of network security solutions in place, but with an ever-increasing amount of network traffic, you need to know that your security tools are keeping you 100% protected.
In this blog, we'll investigate in detail the different types of fundamental measures an organization should take to safeguard incoming and outgoing traffic throughout their company network. We'll cover the various tools and different levels of protection an organization should implement to protect their network traffic.
Image source: Externetworks
What is network security?
The term 'network security' is an all-encompassing, umbrella concept that describes different types of software and hardware solutions. It also refers to the processes or security rules and configurations relating to network use, secure network access, and overall threat protection within company networks.
Security teams need to consider a number of aspects. Implementing effective network security involves:
-
Network access control (the management of authorized users permitted to access corporate data and resources)
-
Virus, antivirus and malicious software
-
Protection against application layer attacks
-
A network's behavioral analytics
-
Endpoint security (protecting devices from intrusion and misuse)
-
Web security (protecting networks and computer systems from hardware and software theft or damage)
-
Wireless network security and Virtual Private Network (VPN) encryption
-
Email security (numerous threats such as scams, malware, suspicious links and phishing can be incorporated in an email)
-
Firewalls
We'll cover these in more detail later.
As well as external threats, organizations are also vulnerable to inside data breaches. In the financial sector for example, an estimated 60% of security threats come from employee negligence or deliberate malicious intention. These types of network security breaches are difficult to control, as the attackers generally have legitimate access control of sensitive data within the organization's network.
How does network security work?
Setting up an efficient and robust network security system always begins with visibility. Without being able to see everything inside your entire network, there's no way you can implement network security tools, or an intrusion prevention system.
Equally important, you need to identify all of your network assets so that you can track, log, and monitor who is accessing your network, what devices are being used, where they are connecting from and when.
Asset management for effective network security
Asset management plays a critical role in a network security system's cyber security operations.
Any device, service or resource within your IT system could be subject to risks and vulnerabilities, so every asset should be identified and categorized according to its value to your business operations. A typical network inventory is made up of:
-
Physical assets: These include hardware devices connected on-site or another physical location, such as servers, printers, mobile devices and workstations.
-
Virtual assets: These include cloud hosted systems like AWS, Azure, Google Cloud etc. or those offered by a Managed Services Provider (MSP).
-
Software: Including open source, closed source, and freeware, as well as software licenses
-
Storage: Any device or computer component used to store data including physical and virtual backup systems, removal storage, network attached servers and cloud storage
Key benefits of network security
The protection and security of client data and sensitive information is important to every organization. Losses that occur from a data breach can have a huge negative impact on a company's credibility, not to mention possible financial disaster.
Cyber-crime statistics
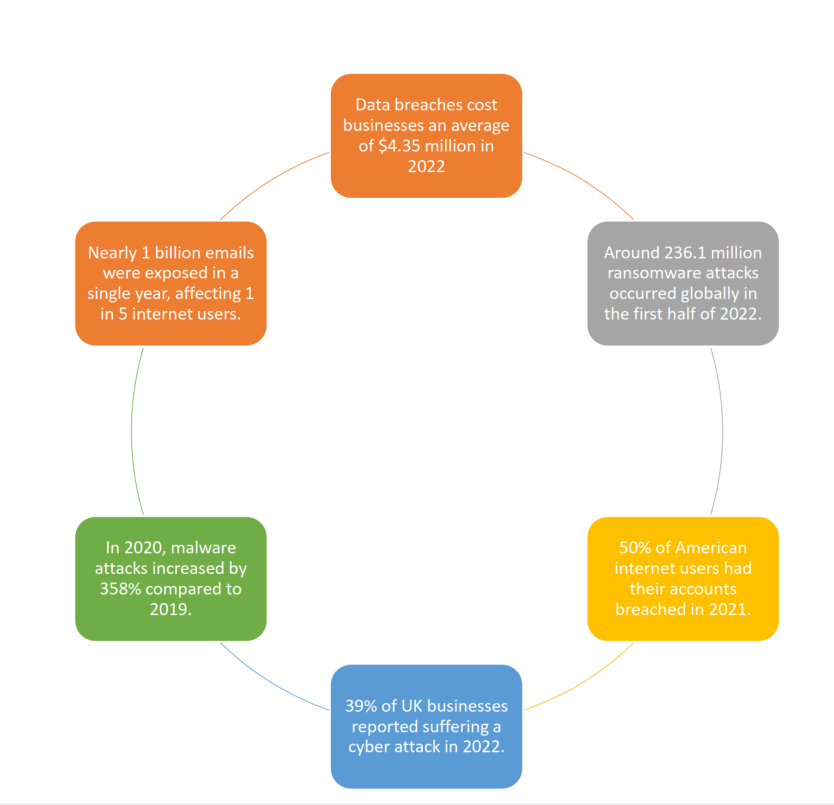
Image Information: AAG
Some of the key benefits of continually assessing and looking to improve network security include:
-
A boost in consumer and client confidence. In a competitive economy, a security breach can affect a business's reputation enormously. Without solid security controls and strong security policies in place, customers at risk will not hesitate to move on - not to mention the legal fallout of a compromise.
-
Compliance. The right network security solution enables a business to stay compliant with government and business regulations.
-
The protection of data and information. Network security ensures the protection of sensitive data shared across an organization's network.
-
Empowering a successful distributed workforce. Proper network security measures enable employees to work securely from any location, as well as allowing the ability to scale with a growing business.
The different types of network security protections
Network security solutions provide a safe environment, allowing applications, clients, and devices to do what they need to do in a secure setting. At the same time, network infrastructure can maintain business credibility by safeguarding private information from attacks.
There are many different examples of network security protection:
Firewalls
Firewalls are now a required component of every network security system. They analyze a computer's incoming and outgoing network traffic looking for any evidence of harmful behavior.
There are several basic types of firewalls, and enterprises may need more than one of them to better secure their systems.
-
Packet filtering firewall
-
Circuit-level gateway
-
Next-generation firewall (NGFW)
-
Application-level gateway (aka proxy firewall)
-
Stateful inspection firewall
Remote access VPN
A remotely accessible VPN encrypts all information sent and received by users, anywhere around the global. It allows safe access by creating a virtual tunnel between the company's network and a remote server. As the information is encrypted, any unauthorized personnel will be unable to access or understand it. There are many advantages of of remote access VPN including cost savings, and Zero Trust Network Access (ZTNA).
Intrusion Prevention System (IPS)
An intrusion prevention system is a network security device that scans network traffic to actively block threats. They may do this by mining data, tracking the path of suspicious files and malware, and prohibiting the spread of outbreaks and preventing system reinfection. Intrusion prevention systems actively block threats by tracking and mining the progression of suspicious files and malware through:
-
The examination of spyware fingerprints on the computer network.
-
Threat detection features that search for evidence of potentially dangerous behaviors.
-
The monitoring of client activity to detect malicious intentions.
Network access control
An organization's network may be used by many people, but not all of them should have the same level of access.
Network access control prohibits access by unauthorized personnel to sensitive areas within the system. Security tools protect each user in each level, providing the ability to limit access to known users and devices and blocking or limiting access to unrecognized devices and users.
Anti-virus and anti-malware software
Antivirus and anti-malware software applications scan and monitor networks for malware the moment they enter the system. They also continuously monitor the network for suspicious behavior and anomalies to help mitigate risk and provide solid protection from viruses, Trojans, spyware or ransomware.
Network segmentation
Network segmentation is a network security measure that divides a network into smaller, more manageable sub-networks, allowing more unique security controls and services to each sub-network. It provides a logical way to safely isolate an active attack before it spreads across the network, by reducing the spread and attack surface to a minimum.
Industrial network security is another sub-category of segmentation, providing added visibility into industrial control systems
Email security
Email security breaches are the most common network security threats. Attackers gain personal information and data through marketing and social engineering techniques to deceive mail recipients into downloading malware, taking part in phishing campaigns, and opening suspicious links.
Email security applications block incoming attacks, filter potential threats, and prevent outgoing emails from sharing certain data and spreading malware through users’ contact lists. While most email service providers have default security features built-in, they may not be enough.
Data Loss Prevention (DLP)
Data loss prevention is a network security technology that identifies and mitigates data leakage, theft or abuse by preventing network users from sharing sensitive data and information with users outside of the network.
Data loss prevention methods can include prohibiting the uploading, downloading, and forwarding of private files, printing private information, or sharing the access codes to classified data.
Cloud security
Cloud providers generally follow best practices to ensure the integrity and security of their servers. The responsibility of protecting data, application security and cloud based workloads however, is also on organizations.
Security threats are more sophisticated as the digital landscape continues to evolve, particularly targeting cloud computing providers due to many businesses having an overall lack of visibility in data access and movement. Organizations need to be proactive about improving their cloud security, or they risk facing significant governance and compliance risks when managing client information, no matter where it is stored.
Sandboxing
Sandboxing is network security tool that works by isolating potentially malicious programs or unsafe codes from the rest of an organization’s environment, so that it can be analyzed safely, without compromising your network's operating system or host devices. If a threat is detected, it can be removed proactively.
Application security
Application security is a measure that aims to prevent data or code within the app from being stolen. This includes software, or hardware that identifies and minimizes security vulnerabilities.
For example, a router that prevents anyone from viewing a specific computer’s IP address from the internet is a form of hardware application security. Software application security includes firewalls that allow or deny access to certain activities.
Finding the right solution
Hybrid and remote working is now an integral of business life, so ever-emerging technology and a landslide of data passes through networks every minute. The demand for security and a seamless user experience, whether it's mobile users or in-office employees is increasing, while the need for high up-time, fast problem resolution, and intelligent insight has never been more critical.
Network security protects your network from potentially lethal breaches of valuable data and network resources. But part of the strategy to achieve this is to have all-seeing eyes on your network at all times.
Stay in control with network performance management tools
The IR Collaborate suite of hybrid-cloud performance management tools can protect your network security by providing you with end-to-end visibility into your entire IT infrastructure.
IR Collaborate can quickly identify, troubleshoot and resolve any issues relating to network security with analytics and insights tailored to your organization. All this in real time, across your on-premises, cloud or hybrid environments.

Watch our Zoom security series
Part 1: Are my Meetings Secure?
Part 2: Are my users' Zoom clients up to date?
Part 3: Are Personal meeting IDs being used?
Part 4: Is Meeting traffic encrypted?



